Multi-Factor Authentication in Smart Home Devices
- March 31, 2022
- by Ezlo Admin
A few important things to consider.
Managing and setting up smart devices requires user authentication to prevent unauthorized access and unwanted actions.
In one of our previous blog posts, we mentioned that some tools allow mimicking a user’s device to intercept their credentials and then use them later to log into an actual device. And this is only one way of many to circumvent password protection; a device can have multiple vulnerabilities allowing theft of passwords or a user’s negligence and ignorance can also be a contributing factor.
Nowadays, a password-only authorization is an insufficient protection from data stealing and data phishing practices. Besides, it becomes simply annoying for users to come up with yet another password for a new device.
To address that, you can replace it with multi-factor authentication.
What’s multi-factor authentication?
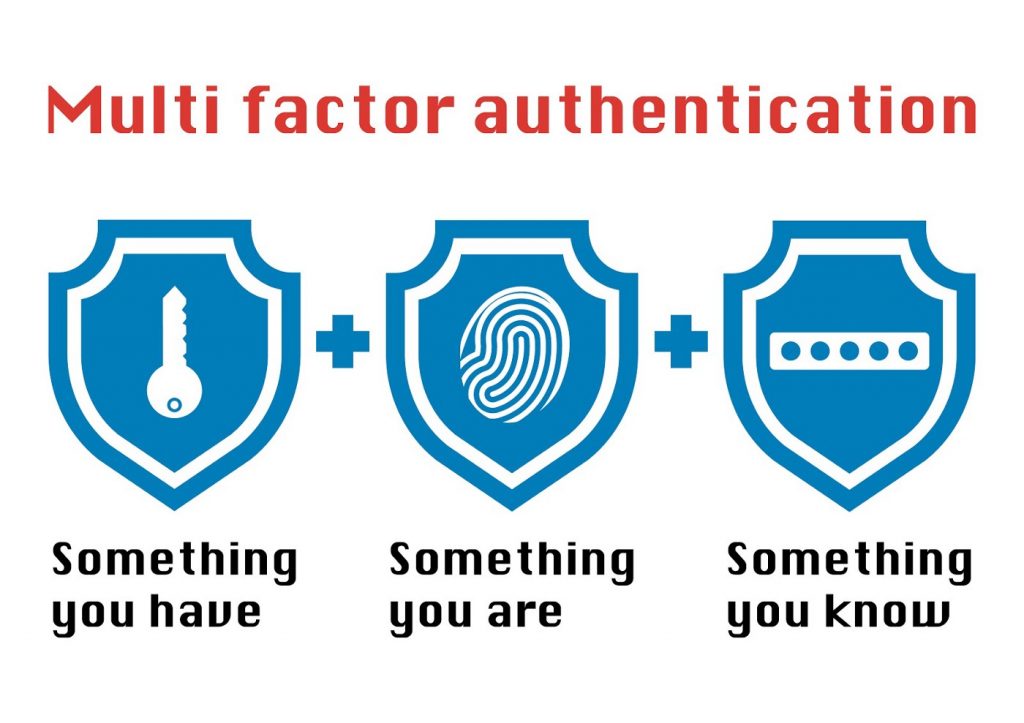
A lead security analyst at PCMAG Neil J. Rubenking splits authentication options into three categories:
- Something you know (like your password or answers to secret questions)
- Something you have (like a smartphone or a smart key)
- Something you are (like a fingerprint or a face)
A multi-factor authentication by its meaning implies that it uses at least two of the above-mentioned options. (So asking a user for a password and, say, a PIN or a secret phrase won’t improve the protection of your device.)
The main rule of multi-factor authentication
While MFA provides a higher level of protection, it also comes with its disadvantages:
- logging in takes more time and effort
- something can go wrong and prevent the user’s access to the device settings
- finally, adding it to the product comes with an additional investment cost
The trick is finding a perfect balance between the required security and usability of improved authentication.
Because if the solution you choose is not quick and convenient enough, users won’t use it. And if it is insecure, culprits may hack it to compromise your users and their data.
Now let’s talk about the types of additional authentication that you can add on top of the password protection.
Authentication Options That Are Currently Available
1. Retinal scans
This biometric technique has been popular in governmental structures like the FBI and CIA for a while now. But during the last few years, many new tools for retinal scans have hit the shelves, making this solution more and more popular.
Still, it’s too early to talk about the wide approval of the technology. The scanners are still pretty expensive (the cheap ones may hurt your eyes); their accuracy may be affected by eye diseases like astigmatism or cataract, and it’s not generally friendly, as users must come very close to the sensor.
The only option where a retinal scan may prove itself worthy that I can immediately think of is a digital peephole.
2. Security tokens
These are usually one-time passwords that a user may receive via SMS or any other messenger or service (one of the most popular is Google Authenticator).
But it can also be a digital key that can talk to the addressed device via Bluetooth or any other available connectivity protocol.
Depending on the nature of the tokens, it may be either simple or complicated for a user to access the necessary information for them. With a digital one-time password, a user is forced to wait before getting the code they need. A physical token should be always with a user for quick access, which might be unnecessary for your device.
3. Fingerprint recognition
After the wide adoption of fingerprint scanning by smartphones, this technology is probably ready to be implemented for an arguably small cost in other devices as well. Generally, it is both quick and secure.
4. Voice recognition
Since there’s a lot of buzzes lately about Amazon Echo and Google Home, eventually your customers will get used to talking to devices, and you can take advantage of it by adding voice recognition.
Nuance reports that its technology analyzes voice for over 140 factors and compares it to a previously recorded voiceprint, and such an approach makes it impossible to duplicate or spoof a user’s voice. But since such biometric authorization hasn’t been adopted by a broad range of users, we don’t know if hackers can deceive it.
5. Facial recognition

Yet another approach that has been widely adopted by smartphones. Since the technology is relatively new, it still requires improvement: you may have heard the reports of iPhone users’ siblings or children can unlock the phone, or that a special mask can be created to trick the system.
If you choose to go with this option, it’s important to provide a flexible and intuitive solution that will work even if users decide to change their haircut, has a boxing match, or experiment with make-up.
6. Gesture-based authentication
Known to many Android smartphone users, gesture-based authentication works best when you need to provide access to your device to a few different people, and you can’t immediately gather them together to add their fingerprints or voices or faces into the system.
7. Behavioral biometrics
A device may track the location of the user when they access their settings remotely and look for patterns. If a user suddenly logs in from a completely new and unknown place, either a message can be sent to notify the user about an unusual login, or additional re-authentication may be requested (or both).
How to choose the best additional authentication method for your product?
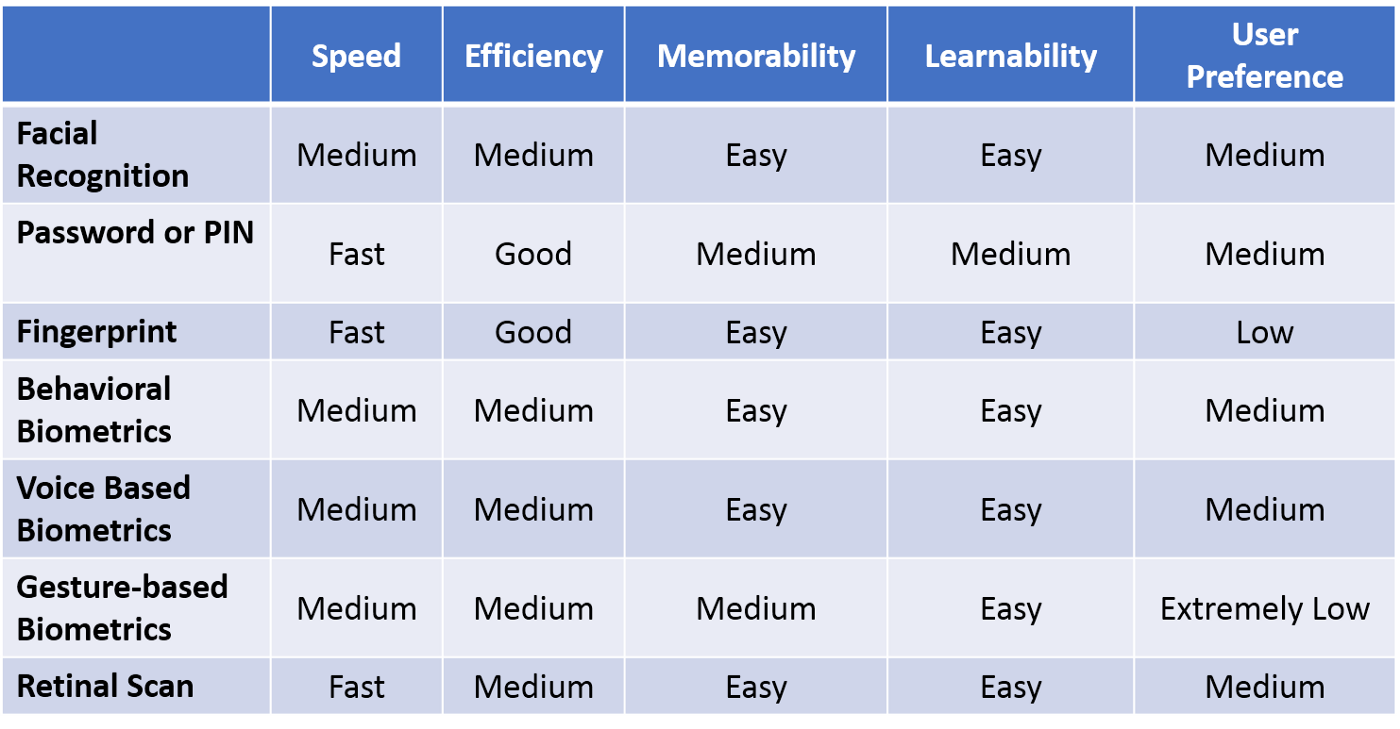
While picking the best way of enabling MFA depends primarily on the way your device is expected to be used, Udit Gupta from Carnegie Mellon University made an informative table that analyzes various authentication methods based on:
- speed: how quick it is for the user to access data using this authentication approach
- efficiency: how reliable and precise the technology is
- memorability: how easy it is for the user to remember the authentication approach
- learnability: how easy it is for the user to learn the process and get used to it
- user preference: how users generally like the offered approach (based on surveys like this one)
We at eZLO went a bit further and updated it according to the latest trends and our understanding of the industry, but feel free to have your point of view on the matter.
While the IoT industry keeps working on the security of its products, enabling multi-factor authentication is the best way to help your users protect their data. Sooner or later, it will be everywhere. The only question is how long your business will hesitate before implementing it.
See Also