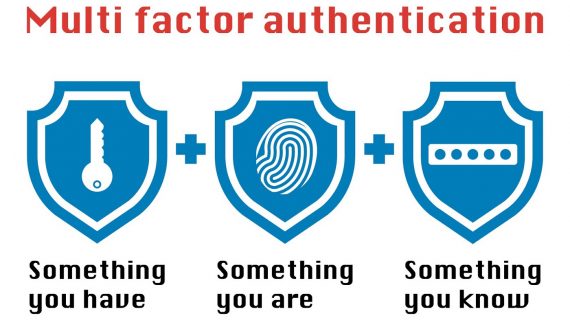
A few important things to consider. Managing and setting up smart devices requires user authentication to prevent unauthorized access and unwanted actions. In one of our previous blog posts, we mentioned that some tools allow mimicking a user’s device to intercept their credentials and then use them later to log into an actual device. And
eZLO Smart Home

5 Key Features of a Smart Home Controller
- by Ezlo Admin
The boom of crisp words, seductive visuals, and smooth packaging in the name of branding kind of concealed our urge to know what really is. Well, who can blame us? When a bright and shiny product is always at our screens and is apparently the talk of the town (in the best sense), resistance is

eZLO Smart Home Goes to GEBT 2016
- by Ezlo Admin
Now on its 13th edition, GEBT — Guangzhou Electrical Building Technology 2016 is the leading exhibition for the electrical engineering and building automation industries in Asia. The GEBT 2016 is going to be held for four continuous days from 9th to 12th June 2016 at China Import and Export Fair Complex, Guangzhou, China. Exhibitors will

Z-Wave: The Most Promising Smart Home Technology in 2024
- by Ezlo Admin
What is Z-Waves? In 2005, Z-Wave Alliance was founded to help standardize the technology and assist vendors with leveraging its advantages. Any home automation configuration requires a communication protocol to allow devices to interact with each other and receive users’ commands. As of 2017, there’s over a dozen of such protocols, and some of them